Four days later...
As soon as my account was restored, new Twitter users followed it in droves. My follower total is now above 10,000, and continues to grow at over 500 per day:
[insert stats page here]
12 hours later...
Less than 12 hours after posting the suspension of my Twitter account, my account was reactivated:
12 hours earlier...
It started with a phone message left by a prank caller, "ordering" a cheese pizza; it ended with the suspension of my Twitter account, with which I had painstakingly cultivated a following of nearly 10,000 Twitter users.
But, first, a transcript of prankster's voicemail, followed by the text conversation that later ensued:
As you can see, it took me a few hours, but I eventually realized that the voice message was a precursor to a demonic issue-in-the-making of some kind. To make sure (and out of curiosity), I sent a text to the number listed with the voicemail in the hopes that I could ascertain any danger he might pose.
Not paranoia, just history
Thinking the person who left the message might possibly be dangerous was not a symptom of paranoid thinking; rather, it was prudence borne of experience. Although I detected no hint of danger, the text conversation was bizarre from end-to-end—just like most conversations I've had with any of the psychopaths that have stalked me ever since the blog began in 2011. Some of those, by the way, have included:
Twitter account suspended one day after prank call
While nothing was cut off, and, as of now, I remain alive (albeit barely), the worst thing to come of things was the next-day suspension of my Twitter account. It came with no warning, save that of the caller:
Not only that, but I found an imposter account, which was replete with veiled racial epithets (not shown):
The question of danger having been brushed aside, the question now became, why?
The relevance of my Twitter account
Aside from their everyday tomfoolery, why did demons and their people consider my Twitter account relevant (or threatening) to them? It's not unreasonable that they would, giving the astounding, yet easy to come by, popularity of blog-related Tweets. At the time of the suspension, I garnered nearly 10,000 followers, and an astoundingly high volume of impressions per Tweet:
The possibilities are two: unwanted exposure, or a popularity that runs counter to their goal of bending my mind in a particular way for some particular reason (I'd be more specific, but I can't be bothered with specifics on that type of nonsense). My guess is both, with the latter more pressing than the former—particularly, given the hundredfold increase in violence against me as of late.
No help from Twitter, as expected
A failure to respond to issues of any kind is characteristic of Twitter support, which goes double for big issues. After notifying Twitter of the problem, I've received no response whatsoever, except an answer to a question I never posed, specifically, how to reset my password.
As I eluded, I didn't expect much, especially given my past interactions involving their refusal to take payment for advertising:
Whenever I have questions about my Facebook ads or the tools used to create and manage them, I get a personal phone call from their support staff, each and every one of which has been competent to a fault.
I feel embarrassed by how little I spend with these companies every time I talk to them, they're that good.
I wouldn't be surprised if I found out that the impersonator worked for the company. That's how such persons work these days, anyway; they don't hack products, they work for the companies that produce them, and introduce problems at the source. I'm convinced my iPhone is proof of this, not just based on the unique problems I've had, but the timing of them [see The Desktop of a Demoniac III]; and, I know for a fact that employees of operating-system vendors build copies to distribute to users unaware a means of causing problems to them. Not only do these builds come from the companies they trust, but the problems they cause are re-introduced whenever reinstalling system software.
As of the time of this posting: no word from Twitter. 10,000 followers, gone, without even a f*ck you.
As soon as my account was restored, new Twitter users followed it in droves. My follower total is now above 10,000, and continues to grow at over 500 per day:
[insert stats page here]
12 hours later...
Less than 12 hours after posting the suspension of my Twitter account, my account was reactivated:
 |
| Although I lost all my previous analytics data, I now have access to my Twitter account again |
It started with a phone message left by a prank caller, "ordering" a cheese pizza; it ended with the suspension of my Twitter account, with which I had painstakingly cultivated a following of nearly 10,000 Twitter users.
But, first, a transcript of prankster's voicemail, followed by the text conversation that later ensued:
 |
| A transcript of a voice message, and the text conversation that followed |
Not paranoia, just history
Thinking the person who left the message might possibly be dangerous was not a symptom of paranoid thinking; rather, it was prudence borne of experience. Although I detected no hint of danger, the text conversation was bizarre from end-to-end—just like most conversations I've had with any of the psychopaths that have stalked me ever since the blog began in 2011. Some of those, by the way, have included:
- a man who issued a death threat by mailing a bullet taped to a note (that eventually led to his arrest by FBI) [see also Court postpones release of serial stalker, cites danger to community];
 |
| From Death threat mailed to former home |
- someone who repeatedly threatened to cut off my penis and my head [see Third death threat adds decapitation to penectomy; see also Second attempt by cyberstalkers to arrange fetishistic trick with male prostitute, propose genital amputation], a not-altogether empty threat, considering that one has happened [see Penile mutilation inadvertently discovered in video], and the other is known to happen [see Demon people fail at attempt to use powers on their own];
- a man who could somehow see me, and otherwise follow me to the places I went—even without being there with me, and even as far away as Indiana [see FBI arrests stalker, detention hearing in federal court next Monday]:
It was on a stormy night during my brief tenure in Indiana last month when the light in my deceased grandfather's bedroom...wouldn't turn on. [Right as] I flipped the switch on the wall [—and then the lamp itself—,] the stalker calls, and, using his scary voice, asks me if I'm "having trouble turning on your grandpa's light?" I said, "I am." He said, "Do you want me to help you?" I paused for a moment, right before eeking out, "Yes". He says, "Try again." So, I flipped the wall switch again. That time, the light came on.
Twitter account suspended one day after prank call
While nothing was cut off, and, as of now, I remain alive (albeit barely), the worst thing to come of things was the next-day suspension of my Twitter account. It came with no warning, save that of the caller:
 |
| Attempting to reciprocate follows of my Twitter account, I discover that it had been suspended for unknown reasons |
 | |
| An impersonator created a Twitter account using my name, as well as photos of me; however, instead of copying the posts to my Twitter feed, the impersonator posted his own |
The relevance of my Twitter account
Aside from their everyday tomfoolery, why did demons and their people consider my Twitter account relevant (or threatening) to them? It's not unreasonable that they would, giving the astounding, yet easy to come by, popularity of blog-related Tweets. At the time of the suspension, I garnered nearly 10,000 followers, and an astoundingly high volume of impressions per Tweet:
 |
| Twitter business was booming just prior to the suspension |
No help from Twitter, as expected
A failure to respond to issues of any kind is characteristic of Twitter support, which goes double for big issues. After notifying Twitter of the problem, I've received no response whatsoever, except an answer to a question I never posed, specifically, how to reset my password.
As I eluded, I didn't expect much, especially given my past interactions involving their refusal to take payment for advertising:
 |
| Latest Facebook ad previews |
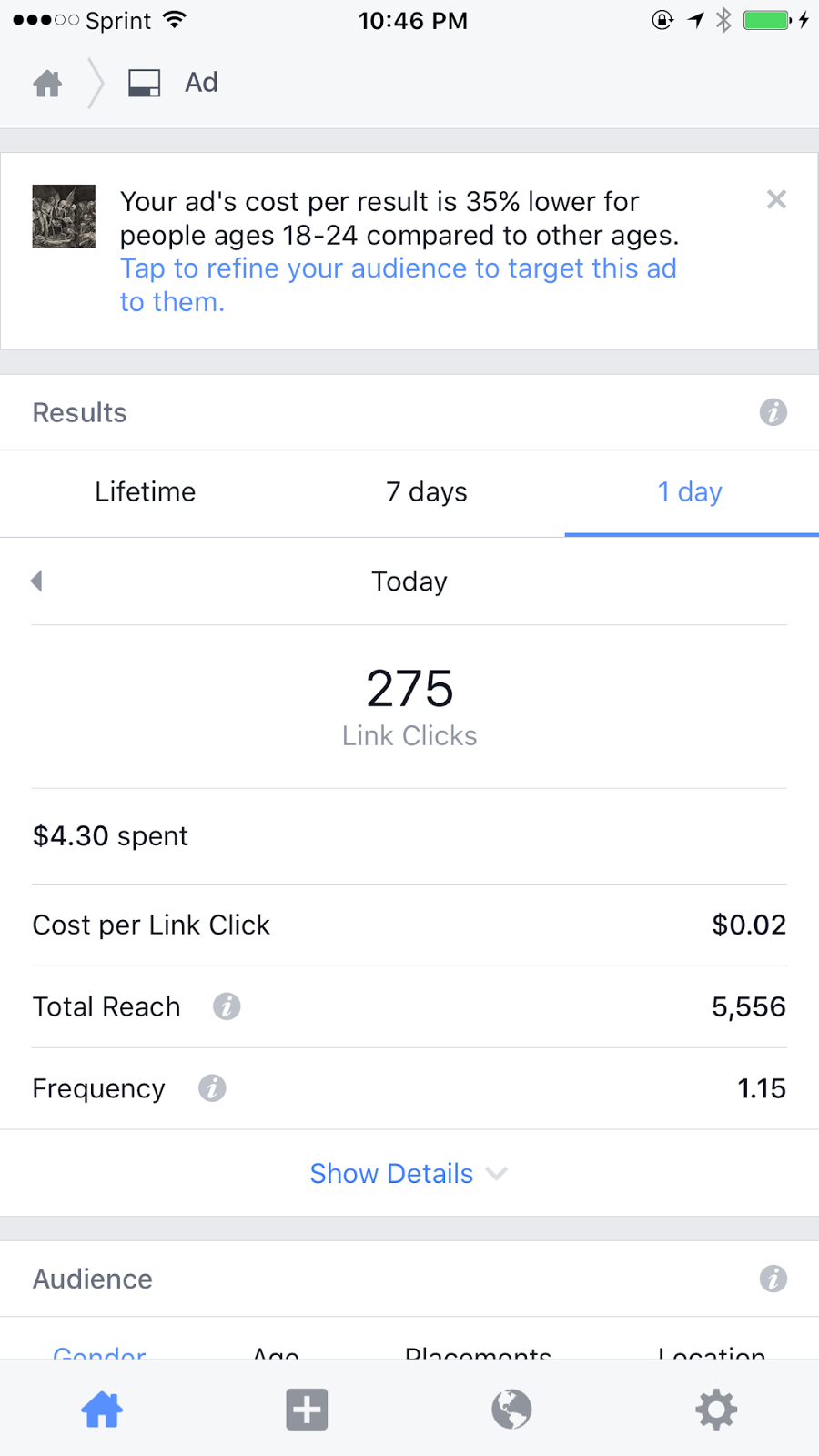 |
| One-day results from the Facebook ad campaign shown above |
I wouldn't be surprised if I found out that the impersonator worked for the company. That's how such persons work these days, anyway; they don't hack products, they work for the companies that produce them, and introduce problems at the source. I'm convinced my iPhone is proof of this, not just based on the unique problems I've had, but the timing of them [see The Desktop of a Demoniac III]; and, I know for a fact that employees of operating-system vendors build copies to distribute to users unaware a means of causing problems to them. Not only do these builds come from the companies they trust, but the problems they cause are re-introduced whenever reinstalling system software.
NOTE | That is a true Trojan Horse attack; but, is less common since, nowadays, most system software reinstallations are performed online (at least with Apple and the Mac). Before this, hackers either obtained pre-silk screened DVDs from the company supply to distribute the malware, or printed the labels onto DVDs themselves. The latter wasn't hard to detect, if you knew what to look for; however, if you had no occasion to be suspicious, you obviously wouldn't look.Still nothing...
As of the time of this posting: no word from Twitter. 10,000 followers, gone, without even a f*ck you.


