Not only do they provide instructions for using your cellphone and computer to aid you, they also keep these otherwise useful tools from being employed to your disadvantage by explaining how technology can be used against you, and what workarounds are available in those situations.
To that end:
- TECHNOLOGY | Demon laptop hack identified, repaired
- TECHNOLOGY | Info + tips on file quality and integrity of demonic activity on video
- TECHNOLOGY | Use Adobe Audition to spy on chatty demons
- TECHNOLOGY | How to build a demon detector with your cellphone
- TECHNOLOGY | Sepia color video camera filter catches more demons
- TECHNOLOGY | Recovering from EVP-related damage to your Huawei Ascend
- TECHNOLOGY | Upgrade your Huawei Ascend M860 (MetroPCS) from stock Android 2.1 to stock 2.2
- TECHNOLOGY | Restore your Huawei Ascend M860 to factory specs (Android 2.1)
- TECHNOLOGY | Huawei Ascend M860 latest modifications tested, working flawlessly
- TECHNOLOGY | Huawei Ascend Upgrade Files
Demonic technology, on the other hand, is more sophisticated than anything described in any work of fiction, leaving only acts of sabotage and preventative measures as viable solutions to the problems they create. Even still, demons can be fought, and they have much to teach.
A three-second clip of a demon displacing air as it moved under cloak allowed for a determination as to the type of cloak some demons use, and, much to their consequence, ways of detecting demons in this semi-invisible state. Specifically, its cloak exhibited the same problems inherent to metamaterial cloaking, which is known to humans; specifically, the problems of refraction, made evident by the strong refraction of the light passing around the cloaked demon (similarly to a prism, which is transparent, but not invisible, because you can see the light bending as it passes through it) and opacity, as light passing through the demon was partially absorbed, making it somewhat opaque (or ghostly). [Source: Wikipedia.org]
In another video, a two-second run-by of one demon that looked unusually smudged and blurred as it ran past [see VIDEO TIMELINE | Hobgoblin Demon Springs From Floor] allowed for the determination of the type of radiation emitted by demons, which lingers after having used a hyperdimensional portal. While that does not have as many applications as knowing about the cloak, it does suggest ways to close or inhibit a demon's ability to move from place to place, instantly, as they have enjoyed for countless years [see Invisible demons detectable by radiation emission; see also VIDEO | Demon with needle-fingered black glove stabs internal organs].
Catching demons on video by surprise
It probably won't work more than a time or two, but, you could conceivably catch demons in your home or anywhere you suspect demonic activity using the iSight camera on your Mac using one of these two applications:
- Quicktime Player, to record video using an Automator script that is run at pseudo-random times via iCal; or,
- Quicktime Broadcaster, to stream video to another Mac via the Apple File Protocol or your local area network (LAN) via Ethernet or a wireless router.
NOTE | If you have an assigned (static) IP address from your Internet service provider, or if File Sharing is setup to share with others outside your network, you do not have to be connected to the same network as the Mac broadcasting video. That means you could spy on your home from anywhere in the world, provided you are connected to the Internet on the receiving end.Following are instructions for setting up these options.
Using Quicktime Broadcaster to spy on demons in real-time
Until my own set of instructions can be provided, you can try this video, which does an excellent job of explaining how to use your Mac to broadcast live video to another computer on your network:
Troubleshooting and other technical questions on the information provided in this video can be answered by theoknock@gmail.com.
TIP | If your network assigns random (non-static) IP addresses, export a reference movie, instead of an SDP file. Then, place the reference movie in the Public folder of the Mac broadcasting video, and turn on File Sharing. Now, any computer that can access the reference movie in the Public folder can watch the broadcast.The settings you use for your setup will depend on the capabilities of your Mac; however, for reference, I have provided the ones that worked best for me (notice behind me that my laptop is receiving the broadcast from the other Mac):
 |
| Audio settings |
 |
| Video settings |
 |
| Network settings |
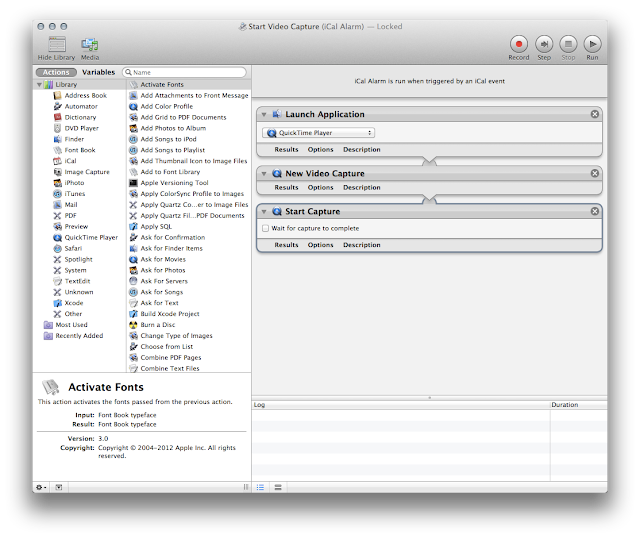
In Automator, create a new Automator action, named Start Video Capture, that will be triggered by an iCal event, and which contains the following Quicktime Player commands:
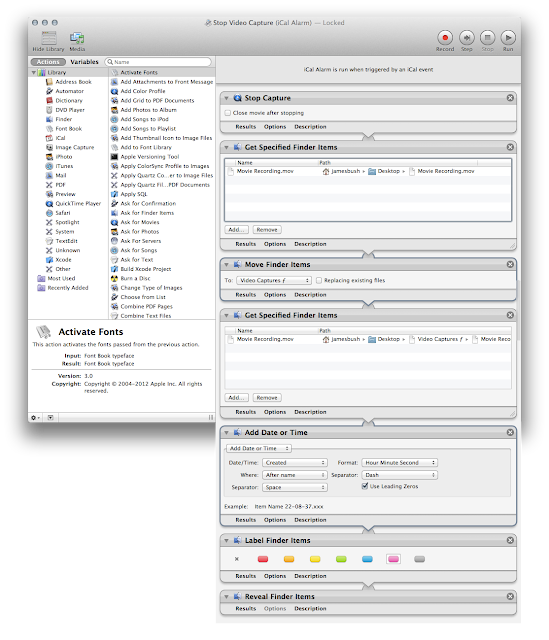
Then, create another Automator action, named Stop Video Capture, that can also be triggered by an iCal event, and which contains the following Quicktime Player and Finder commands:
In the Finder, create a new folder on the Desktop, named Video Capture ƒ (Option-f); then, in iCal, create a new event, which triggers the Start Video Capture action at the time and day of your choice:
Then, create another iCal event that triggers the Stop Video Capture action at a later time:
NOTE | Of course, the length of time between events should be based on an estimate of available free disk space.Create new events for each time you want to record video:
 |
| Staggered pairs of Start and Stop triggers in iCal, designed to catch demons on video unawares |